Why the NDAA Ban on Chinese Surveillance Tech Is a National Security Lifesaver (and Why You Should Cheer It On)
The NDAA’s ban on Chinese cameras isn’t about trade wars — it’s about defending U.S. sovereignty from espionage. Here’s why the ban matters, why critics are wrong, and how ArcadianAI represents the next evolution in secure, AI-driven surveillance.

Introduction
In an era when cameras are no longer just “eyes” but networked computers, the risks of compromised surveillance equipment are too great to ignore.
That’s why the National Defense Authorization Act (NDAA) Section 889 and related federal actions banned equipment from Hikvision, Dahua, Huawei, ZTE, and Hytera. These companies are not neutral vendors — they are arms of the Chinese state, supplying technology tied to espionage, censorship, and human rights abuses.
Critics say the ban is “protectionism” or “fear-mongering.” But cybersecurity professionals, U.S. intelligence agencies, and global allies know better. Cameras with opaque firmware and hidden update channels are Trojan horses. Once embedded in critical infrastructure, they can be exploited to disable feeds, exfiltrate data, or worse — open the digital backdoors that foreign adversaries need.
At ArcadianAI, we see the NDAA not as a barrier, but as a catalyst: a chance to rebuild surveillance on trusted, transparent, camera-agnostic AI platforms like Ranger, designed for compliance, resilience, and smarter protection.
This post will dissect the NDAA ban, explain why it’s not just good but essential, and show how enterprises can embrace this new era of cybersecurity.
Quick Summary / Key Takeaways
-
NDAA bans Hikvision, Dahua, Huawei, ZTE, and Hytera from U.S. federal systems.
-
The ban protects against espionage, backdoors, and human rights abuses.
-
Critics cry “protectionism,” but this is about sovereignty and security.
-
Allies like Canada, Australia, and the U.K. are following suit.
-
ArcadianAI is NDAA-clean, camera-agnostic, and future-proof.
Background & Relevance
What Is the NDAA and Section 889?
The National Defense Authorization Act for Fiscal Year 2019 included Section 889, which prohibits U.S. government agencies and contractors from:
-
Procuring new equipment from Hikvision, Dahua, Huawei, ZTE, and Hytera.
-
Using equipment from these companies on any federal project or contract.
Later reinforced by:
-
The Secure Equipment Act of 2021, instructing the FCC to deny authorizations for high-risk devices.
-
The FCC 2022 ban on new Hikvision/Dahua authorizations.
-
Directives from the Department of Defense (DoD), Department of Homeland Security (DHS), and Office of Management and Budget (OMB) requiring federal contractors to certify NDAA compliance.
Why It Matters in 2025
-
AI-enabled cameras can now do facial recognition, behavior analysis, and thermal imaging — amplifying risks.
-
U.S.–China geopolitical rivalry has intensified, from chip bans to TikTok restrictions.
-
Cyberattacks on infrastructure are increasing, with IoT devices often the weak link.
The NDAA ban is part of a broader cyber defense doctrine: treat supply chains as national security assets.
Core Exploration
1. The Chinese Brands at the Center of the Ban
-
Hikvision — The world’s largest surveillance camera maker, partially state-owned, tied to surveillance in Xinjiang. Sanctioned by the U.S. Treasury.
-
Dahua — Another Chinese surveillance giant, providing AI tools used in China’s domestic monitoring campaigns.
-
Huawei & ZTE — Telecom firms accused repeatedly of installing backdoors into 5G and LTE equipment.
-
Hytera — Radio communication manufacturer implicated in IP theft and espionage cases.
These firms are not simply “cheap suppliers.” They are enablers of Beijing’s domestic repression and potential vectors of global espionage.
2. Why Cameras Are More Dangerous Than You Think
A modern CCTV or IP camera isn’t just a lens. It’s a miniature computer with:
-
Embedded processors
-
Operating systems
-
Network stacks
-
Remote update capabilities
When the firmware is written by companies tied to adversarial governments, the risk is obvious: those cameras can spy on you, your networks, and your data.
Reports have shown:
-
Hikvision devices phoning home to Chinese servers.
-
Dahua cameras shipping with hard-coded backdoors.
-
Exploitable flaws that allow attackers to seize control of cameras remotely.
For a government building, airport, or power plant, this isn’t a nuisance — it’s a critical threat.
3. The Critics’ Case (and Why They’re Wrong)
Criticism 1: “It’s protectionism.”
Rebuttal: The U.S. hasn’t banned all Chinese goods. It banned specific companies with national security risks. This is defense, not economics.
Criticism 2: “It raises costs.”
Rebuttal: Short-term, yes. But the cost of replacing cheap Hikvision cameras is nothing compared to the cost of a federal breach.
Criticism 3: “Other countries won’t follow.”
Rebuttal: Wrong. Australia, Canada, and the U.K. are actively stripping Chinese cameras from government offices.
Criticism 4: “Not all Chinese devices are bad.”
Rebuttal: True. But given opaque supply chains, blanket bans are the only practical safeguard.
4. The Global Domino Effect
-
Australia (2023): ordered removal of Hikvision and Dahua from federal offices.
-
Canada (2024): ordered Hikvision to shut down domestic operations.
-
U.K.: launched audits and restrictions on Chinese cameras in sensitive sites.
-
European Union: increasing scrutiny of Chinese ICT supply chains.
The NDAA set the precedent. Allies are catching up.
5. Industry Fallout: How Competitors Responded
-
Genetec: shifted marketing to emphasize NDAA compliance and “trusted supply chains.”
-
Milestone: auditing OEMs to reassure customers.
-
Eagle Eye Networks: distancing from Chinese hardware, but still cloud-based, limited analytics.
-
Verkada: pitches itself as U.S.-based, but faces criticism for closed, lock-in hardware.
-
Ring / Nest: consumer-focused, not designed for federal or enterprise compliance.
Most of these platforms are scrambling to distance themselves from Chinese components.
ArcadianAI, by contrast, was born clean.
Comparisons & Use Cases
Case Study 1: DHS Facility
A Homeland Security site uses Hikvision cameras. During a cyberattack, adversaries exploit a firmware backdoor, disable perimeter feeds, and move laterally into networks. With NDAA bans, this attack surface shrinks dramatically.
Case Study 2: Federal Contractor
A defense supplier with Dahua cameras loses eligibility for contracts. After replacement, compliance is restored — but only at high cost. Lesson: compliance must be proactive.
Case Study 3: Municipal Government
A city police department funded by federal grants unknowingly uses banned cameras. Auditors force replacement, causing financial and reputational damage.
ArcadianAI: The NDAA-Clean Alternative
ArcadianAI’s Ranger platform provides:
-
Camera-agnostic integration (Axis, Hanwha, Bosch, Avigilon, Uniview NDAA-compliant).
-
Cloud-native AI — eliminating risky firmware dependencies.
-
SOC 2–ready compliance — built for enterprise IT standards.
-
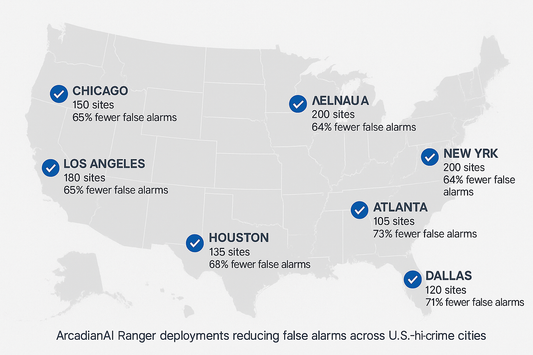
False alarm reduction (up to 65%) — saving police, insurers, and businesses time and money.
-
Global readiness — supporting U.S., Canadian, and EU compliance frameworks.
While others react to bans, ArcadianAI was designed to never depend on banned technology.
Common Questions (FAQ)
Q1: Does NDAA affect private businesses?
Indirectly. While private buyers can still use Chinese gear, they risk cyberattacks, insurance penalties, and contract ineligibility.
Q2: How do I know if my cameras are NDAA compliant?
Check if they originate from Hikvision, Dahua, Huawei, ZTE, or Hytera (or subsidiaries). White-labeled devices count too.
Q3: What if I already installed Hikvision/Dahua?
Replace them if you want federal eligibility. Otherwise, accept ongoing cyber risk.
Q4: Do allies enforce the same bans?
Yes. Australia, U.K., and Canada are actively removing Chinese cameras.
Q5: Is ArcadianAI NDAA compliant?
Yes. ArcadianAI is camera-agnostic and avoids any banned hardware dependencies.
Conclusion & Call to Action
The NDAA ban on Chinese surveillance tech is not paranoia — it’s pragmatism. In a world where adversaries weaponize firmware, trusting opaque systems is reckless.
The ban is a shield for sovereignty, a catalyst for innovation, and a wake-up call for anyone still clinging to cheap gear.
ArcadianAI is ready for this world: NDAA-clean, cyber-resilient, and powered by Ranger’s AI analytics.
See ArcadianAI in Action → Get Demo – ArcadianAI
Security Glossary (2025 Edition)
AI Analytics — Algorithms that detect events or anomalies in video feeds.
Backdoor — Hidden method to bypass security controls.
Dahua — Chinese surveillance manufacturer banned under NDAA.
FCC Ban (2022) — FCC prohibition on new authorizations for Chinese surveillance equipment.
Hikvision — World’s largest surveillance maker, banned from U.S. federal use.
Huawei — Chinese telecom firm linked to espionage.
Hytera — Radio comms company banned for espionage risks.
NDAA Section 889 — Provision banning procurement/use of covered Chinese surveillance gear.
Supply Chain Security — Verification of components, firmware, and manufacturing origin.
Zero Trust Security — Assumes no device is trustworthy by default.

Security is like insurance—until you need it, you don’t think about it.
But when something goes wrong? Break-ins, theft, liability claims—suddenly, it’s all you think about.
ArcadianAI upgrades your security to the AI era—no new hardware, no sky-high costs, just smart protection that works.
→ Stop security incidents before they happen
→ Cut security costs without cutting corners
→ Run your business without the worry
Because the best security isn’t reactive—it’s proactive.